The business strategy teachings of Michael Porter (1) are core to any MBA program, and within those teachings, the “value chain” is critical to defining and optimizing business operations.
The value chain includes supply chains, internal operations, distribution, and payment gateways, all related to creating and delivering a product or service to market. In cybersecurity, we hear a lot about supply chains, vendor risk, third party risk, and payment gateway risk – all of these risk areas fall within a company’s value chain.
Last week I met with the IT team from a dairy farming cooperative, and the conversation immediately focused on cybersecurity risk within their value chain. Two risks were of primary concern were sharing of account, PII, and pricing information as products journeyed from the farm to the grocery store and customer (the supply chain), and sharing of PII and payment information that flowed in the opposite direction, from the consumer back to the farm (payment gateway chain).
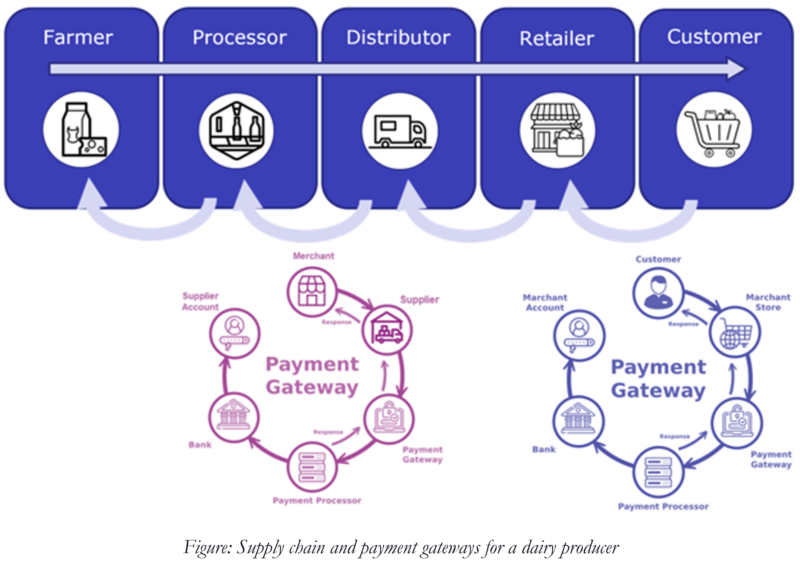
As the Dairy Farm’s IT team explained, “The larger and more sophisticated the food processing company, distributor, or retailer we can work with, the more revenue we can generate for the Coop. At the same time, the cybersecurity compliance requirements of each organization are more strenuous. If we can not show compliance to their requirements, we will not close these lucrative contracts.”
Increased cybersecurity requirements are put in place by participants in the supply chain to lower the risk of cyber attacks. As CISA(2) states, “3rd party risk is probably the greatest threat any company faces today when dealing with cyber security threats. Instances of sub-tier suppliers or ancillary vendors with poor cyber hygiene who inadvertently allow for the breach of a much larger company are well documented.”
For this Dairy Coop, cybersecurity had become a critical concern for the business. The business leaders were pushing the IT team to find a solution which would allow the Coop to close contracts with the larger supply chain companies and increase revenues.
The question became How? – how could the Dairy Coop show their supply chain partners that their IT environment and data is secure and would stay secure?
In what we could call “Big C” compliance, things like PCI-DSS, PSD2, and AML. These government-enforced regulations have specific control and audit requirements and usually require an annual third-party audit. Although the Dairy Coop had to meet those requirements, what was really troubling them was what we can call “Little c” compliance. The compliance requirements derived from “Big C” compliance and implemented as best practices for their third-party vendors with one huge caveat – they wanted to show compliance every single day of the year, not just during an audit.
That challenge of showing consistent and effective cybersecurity controls became the root of the problem. Yes, the Coop’s cybersecurity controls worked all the time, but with a formal audit, you have weeks to prepare reports, and in the supply chain requirements, you do not. To address the problem, the Coop must deploy a platform that monitors what is happening across cloud, network, user, and endpoint devices. It must also have an automated reporting system to capture and record the status of various controls as well as the overall health of the environment. Most importantly what was needed is an internal scorecard report of what is happening at any given moment. To finish the conversation, the IT Team at the Dairy Coop reminded us that the entire team consists of 18 staff, no SOC, no SIEM, no ability to hire new staff, and a tight budget.
Over my years in the industry, I have often heard complaints that cybersecurity impedes business and is nothing more than an expensive insurance policy, but this discussion proves otherwise. In fact, with the increased IT integration of value chains across industries globally and the ubiquitous cyber attacks against these value chains, cybersecurity should be seen as an enabler of digital business. IT and security leaders as well as business leaders today must work together to implement business plans that include risk mitigation and cybersecurity processes.
You are operating your business at an extreme disadvantage if you are not.
As for the Dairy Coop, that problem was straightforward for CyGlass to solve, and this organization is one of our newest customers.
Deploying as a 100% cloud-native platform, with 24×7 monitoring of network, cloud, M365, AD, Azure, and AWS environments (endpoint integration is imminent), and with automated reporting across all of those environments, CyGlass met 100% of the Coop’s requirements. We deployed less than an hour into their environment, operating efficiently for the existing team and coming in under budget.
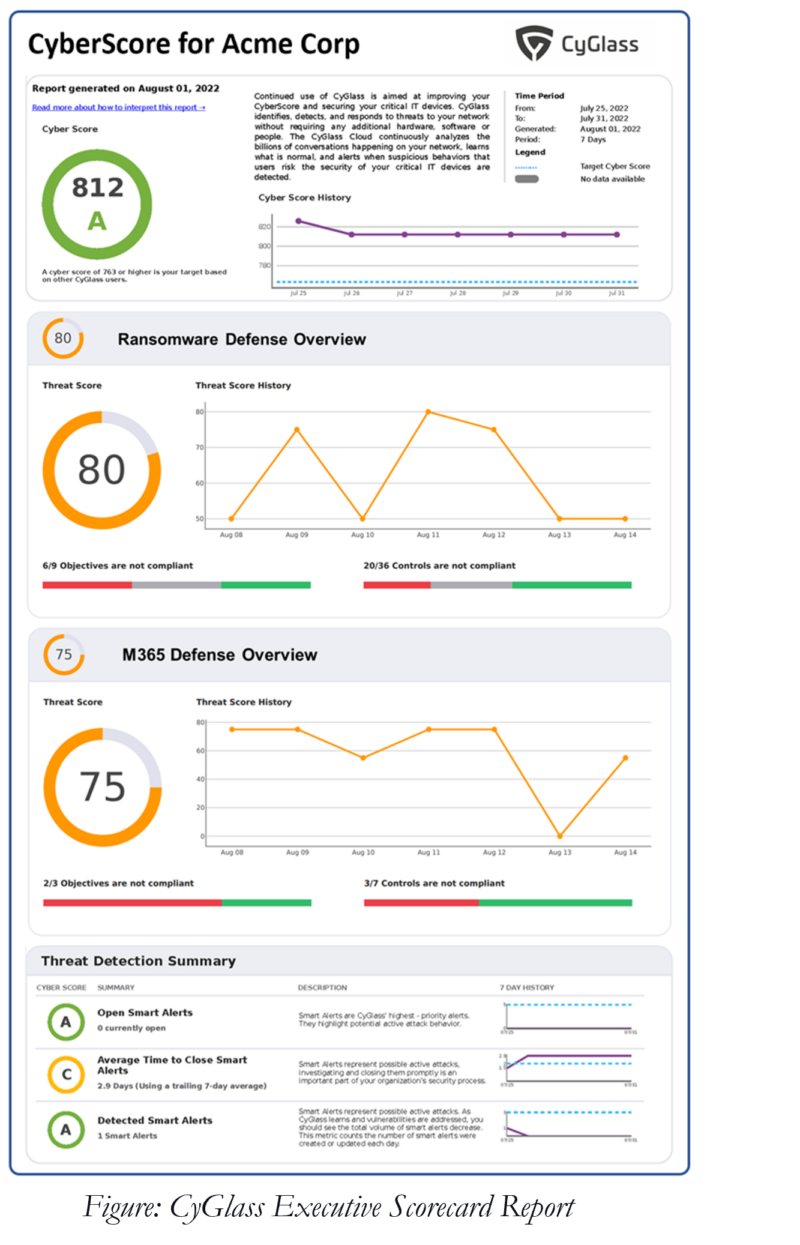
The Dairy Coop now has an automated scorecard report that gives an overview of its network and cloud environment. The reports update daily and can be run on-demand.
Learn More About 24X7 Control Monitoring and Reporting with CyGlass.
- Michael Porter is an economist, researcher, author, advisor, speaker and teacher of business strategy at the Harvard Business School.
- CISA: Cyber Infrastructure and Security Agency, is part of the US Department of Homeland Security.
Bill Munroe
VP Marketing, CyGlass