The Common Vulnerability Scoring System (CVSS) is a framework used for communicating the severity of software vulnerabilities and the characteristics of the same. The range of 9.0-10.0 indicates SigRed is not only in the “Critical” level but has the highest possible score. When malware is described as “wormable”, that means it can propagate automatically without human intervention so it can spread throughout a network with incredible speed. So what can you do to prevent SigRed from impacting your environment? The best way is to patch for prevention and monitor using CyGlass to ensure your network remains secure and available so your business can continue to grow and deliver value to customers.
CyGlass uses cutting edge AI/ML algorithms to give businesses key insights into network activity, alerting customers of abnormalities that may indicate network threats. CyGlass is a hands-off solution always monitoring your network so you can focus on what you do best — running your business. If your organization is unable to install the new Windows patch for SigRed immediately, there is a registry workaround all organizations should use in the absence of patching. However, even after patching and other preventive methods are put in place, it is critical to continue monitoring your environment for SigRed and other wormable exploits as they can bring your operations to a halt. Let’s dig into the specifics of how CyGlass can work for you when it comes to keeping your network safe.
While many antivirus solutions, intrusion prevention systems (IDS) and intrusion prevention systems (IPS) require a malware signature for detection, CyGlass uses machine learning technology to develop a baseline of your systems and bring key abnormalities to your immediate attention, even if they are attributable to new strains of malware without a known signature. A zero-day exploit, or one without any known signatures, can be difficult to detect in your environment unless you use a product like CyGlass.
Based on what we know about SigRed, it creates abnormal activity over DNS or port 53 using the TCP protocol. CyGlass is designed to monitor for such behaviors and notifies customers by sending an email alert. You can investigate the alert by clicking the link sent to your inbox which will take you to the “investigate” page.
This alert behavior presents you with important context before viewing the NetFlow data:
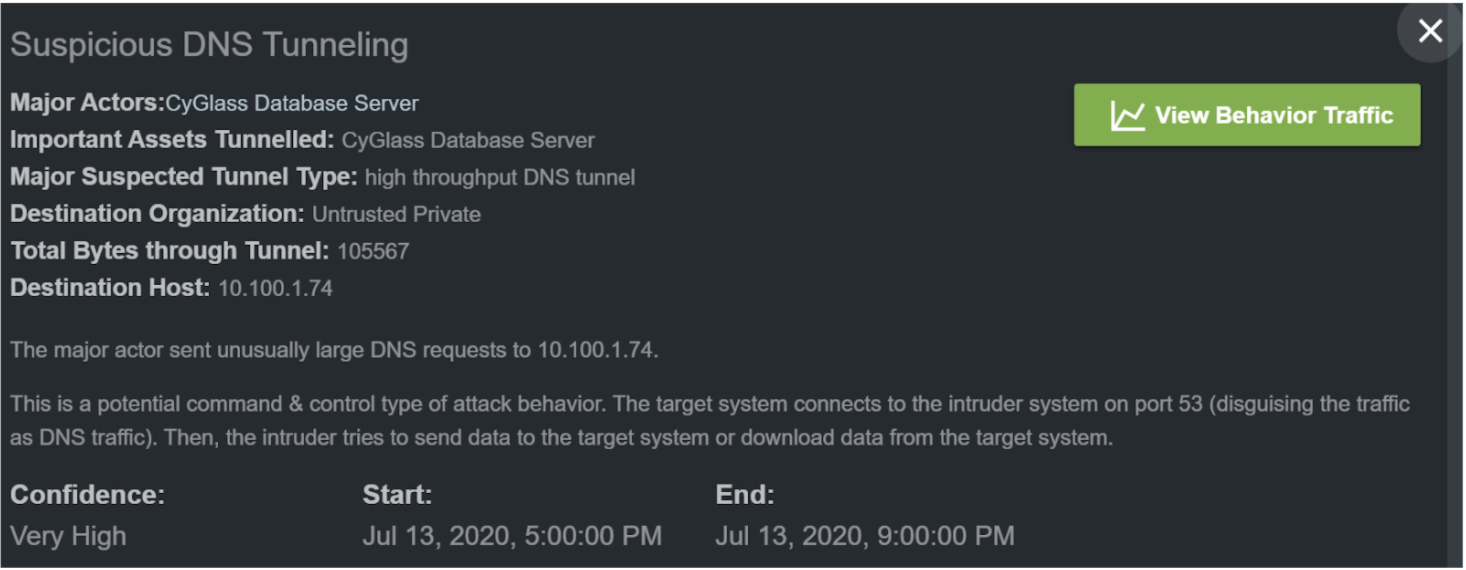
The most important information in this window is the major actors, the total bytes through the tunnel, and the suspected tunnel type. Now that you have a better understanding of the behavior, it helps to have a visualization of where the data is going and how it is interacting with various systems across your environment. CyGlass provides you the behavior map in the same window just below this information to automate this process and make it easy for you to gain an immediate and intuitive understanding of what the behavior looks like in your unique environment.
Now that you have an overview and a map of the activity, it’s time to dig in deeper to ascertain whether it’s time to activate your incident response procedures or not. Selecting the “View Behavior Traffic” icon within CyGlass enables you to do exactly that. When it comes to drilling down into specific ports, protocols, timeframes, assets, nodes, related alerts, and other NetFlow information, the CyGlass Investigate Traffic pane has everything you need.
Start by filtering port 53 for TCP DNS connections or requests to examine the protocols and behaviors occurring. CyGlass will automatically filter data to show the threat, but also enables each user to customize the search so you can get the exact information you want:
 With the search parameters populated, we can see the results over time to see how the communication unfolded. The chart below shows the DNS related external traffic over time:
With the search parameters populated, we can see the results over time to see how the communication unfolded. The chart below shows the DNS related external traffic over time:
Visualizing DNS TCP communications, which are a hallmark of SigRed, can help provide context to the communication, adding more information to help your organization determine whether a closer or vendor engagement is merited. CyGlass was able to quickly detect the unusual observed behavior and alert automatically, show which IP’s and network devices were involved, and identify the source of the traffic. The IP information is shown in the communication flow above and captured in the network Behavior Map shown earlier.
As attackers become more skilled, it is critical to improving your organization’s security posture beyond just relying on known malware signatures. CyGlass provides its customers with cyber safety against threats without known signatures, or zero-days, like SigRed. Contact the CyGlass team today to see how your organization can bring better value to shareholders by avoiding costly breaches and time-consuming post-incident remediation.